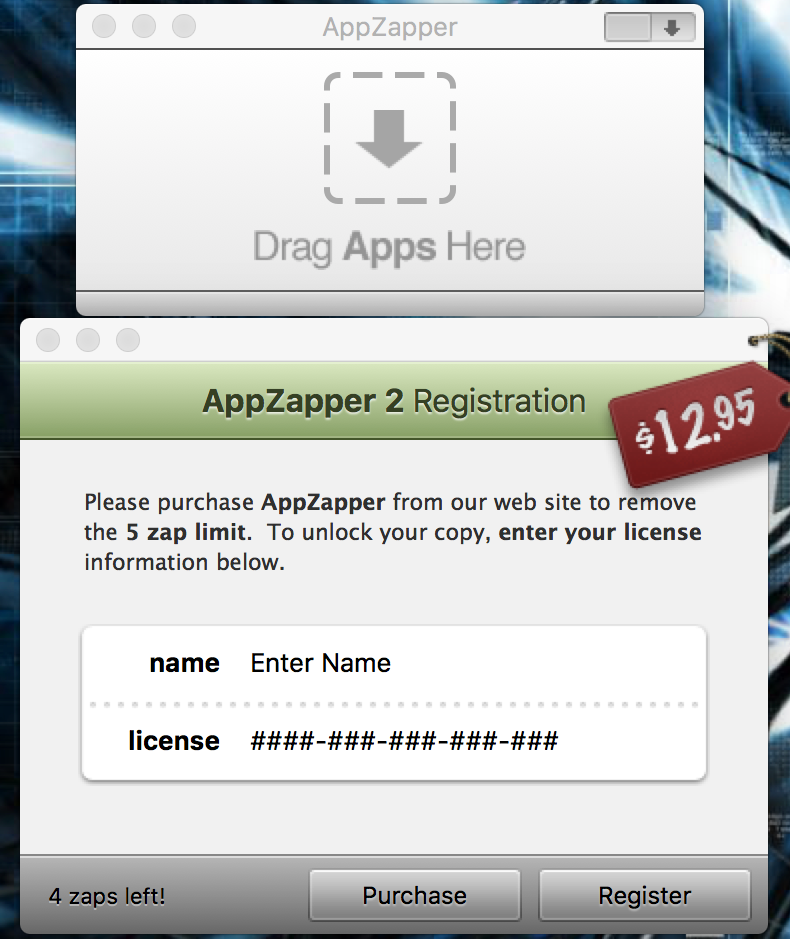
It had be a while that I touched any assembly code. So I thought I will refresh and have some fun while at it. Hopper is a disassembler for macOS. It has call flow graphs and pseudo code. Another awesome thing is the themes, which adds a modern touch, and is easy to use. This is more about using Hopper for disassemble and patching Mac OS X binaries. So let's get started. For that I will choose a real app. There was a case where I had to downgrade iTunes once. For that I had to use AppZapper. When you open it you can see the nag screen. But removing the nag is simple.
Open the app in Hopper. The AppZapper package has only one binary file AppZapper. Proceed with the default choices, i.e., for the package the loader is FAT archive x86-64 bit and for the executable it is Mach-O 64 bits. It shows the entry point procedure at address 0000000100000f60. Before proceeding, enable "Show the HEX column" to easily see the hex of the instruction set, like in OllyDbg.
Now from the left symbols panel, under Proc. choose -[AZAppController applicationDidFinishLaunching:] the idx of which is 88. Alternatively you can directly go to the address of the proc at 000000010000a250. Choose the pseudo code mode from the toolbar to get an idea of what is happening.
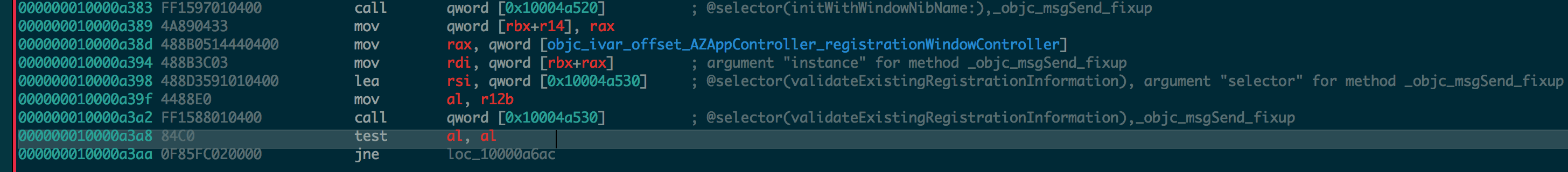
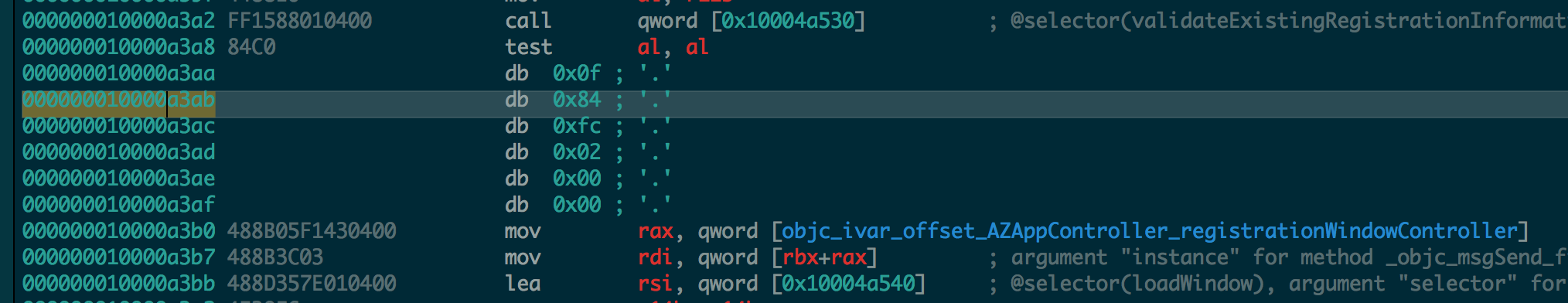
What it does is that it loads the AZRegistrationWindowController and calls the validateExistingRegistrationInformation method whose return value is in rax register. Then it takes the lower bytes of the ax register and performs a bitwise and (the test instruction). If the result is 0, means al is 0, then the zero flag (ZF) is set. If zero flag is not set, then do a local jump to the address at loc_10000a6ac which is at 000000010000a6ac. What we need to do is to take that branch which will then skip loading the AZRegistrationWindowController window. To do that we need to change the jne instruction to je. So the easy way is to click on the jne line and click the hex mode, which will highlight the instruction. The hex for jne/jnz instruction is 85 and hex for je/jz is 84. So double click 85 in instruction 0F 85 FC 02 00 00 and replace it with 84. Go back to asm mode and you can see the updated instruction. Only that it is shown in bytes (db).
Now we need to export the binary. From File menu choose Produce new executable and save as AppZapper. Go to applications, control click AppZapper and choose Show Package Contents and navigate to MacOS. Now replace the executable with the patched one. If you want to preserve the original then, rename that to something else and copy the patched one as AppZapper. Open the app, and we are no longer greeted with the nag screen!
But hey, we still got to register and have only 5 zaps, so we will have to purchase if we need to continue using. The register option is available from the menu.